The Hidden Costs of Cloud Convenience
Cloud computing is now the backbone of enterprise modernization. From healthcare and banking to manufacturing and logistics, every industry is moving workloads to the cloud to gain scalability, agility, and operational efficiency. Yet, behind the efficiency narrative lies a quieter reality, one that too many organizations realize too late.
According to IBM’s Cost of a Data Breach Report 2024, 82% of breaches involved data stored in the cloud. The issue isn’t the cloud itsel,f it’s the assumption that the provider’s infrastructure equals security. In truth, the most common cloud security challenges stem from enterprise-side oversights, not provider vulnerabilities.
As companies accelerate their cloud migrations, often through fast-paced AWS cloud migration or multi-cloud deployment, critical gaps appear in governance, visibility, and compliance. These gaps don’t just expose data; they undermine trust, disrupt operations, and in some cases, erode years of digital progress.
This article examines seven security gaps enterprises routinely overlook when selecting a cloud provider, and explains how to address each through strategic, sustainable security practices.
1. Limited Visibility Across Multi-Cloud Environments
The Problem
The multi-cloud approach offers flexibility and vendor independence, but it also fragments visibility. Each cloud provider, whether AWS, Azure, or Google Cloud, operates with its own console, monitoring framework, and policy definitions.
In large enterprises, this leads to visibility of silos. Security teams often manage dozens of dashboards but still lack a unified view of assets, access controls, and configuration states.
A 2024 Flexera report found that 80% of enterprises operate across more than one cloud, yet only 38% have complete visibility into workloads and data flows.
The Learning
Visibility is not just about dashboards; it’s about consistent governance. Without integrated visibility, you cannot measure or improve security posture, nor ensure compliance across regions and workloads.
The Fix
Implement Cloud Security Posture Management (CSPM) tools to automatically monitor configurations and detect deviations across multi-cloud environments.
Combine CSPM with centralized logging and SIEM integrations for real-time insights. This ensures that compliance (like ISO 27001 or GDPR) is not reactive but continuous.
2. Misconfigurations During Cloud Migrations
The Problem
Misconfiguration remains the most frequent and expensive cloud security challenge. In rapid cloud migration services, configuration errors can open storage buckets, disable encryption, or mismanage IAM permissions.
Gartner estimates that 99% of cloud breaches will result from customer misconfigurations by 2026. During complex AWS cloud migration projects, these errors often occur due to automation scripts, legacy architecture, or human oversight.
The Learning
Automation without validation is a risk at scale. Every migration phase, from data transfer to application deployment, introduces security complexity. Treat configuration reviews as mandatory checkpoints, not optional audits.
The Fix
- Establish a migration security baseline before moving workloads.
- Conduct automated compliance scans using tools like AWS Config, Azure Policy, or third-party scanners.
- Involve security engineers in the cloud migration service lifecycle, not just after deployment.
- Validate IAM roles, storage access, and encryption policies before production cutover.
The result: predictable, repeatable, and compliant migrations that don’t compromise resilience.
3. Misunderstanding the Shared Responsibility Model
The Problem
One of the most persistent misconceptions in cloud adoption is that the provider manages all aspects of security. While providers secure infrastructure data centers, physical servers, and hypervisors, customers remain responsible for application-level security, configurations, and data protection.
Many enterprises still operate under the illusion that migrating to AWS or Azure automatically ensures compliance and protection. This assumption often results in unpatched workloads, weak access management, and compliance violations.
The Learning
The cloud is a partnership, not a transfer of accountability.
Security failures rarely happen because of a lack of tools, they happen because ownership boundaries are unclear.
The Fix
Create a Shared Responsibility Matrix outlining who is responsible for each security function, from encryption key management to API security.
Review this matrix quarterly with both internal and vendor teams.
Ensure that your cloud compliance framework explicitly references shared duties, particularly for industries governed by HIPAA, GDPR, or ISO 27001.
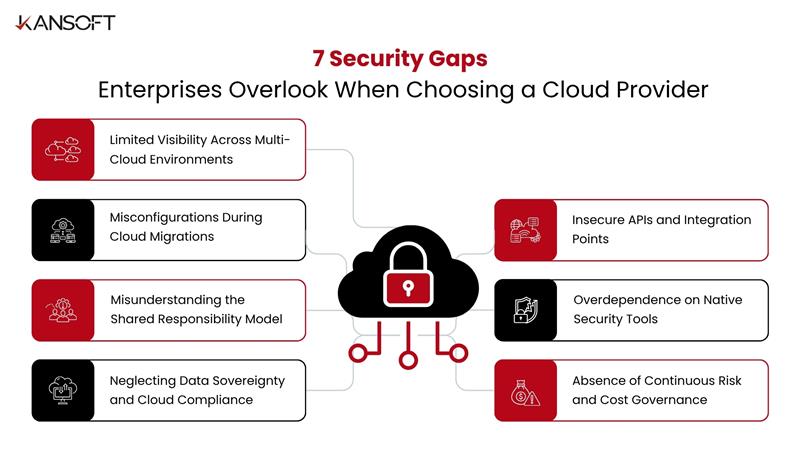
4. Neglecting Data Sovereignty and Cloud Compliance
The Problem
Data sovereignty, where and how your data is stored, is one of the most underestimated aspects of cloud security. When enterprises choose cloud providers based solely on performance or pricing, they risk violating regional compliance laws.
An IDC Europe report (2024) revealed that 32% of European organizations faced compliance challenges after cloud migration due to unclear data residency practices.
This risk is especially acute in highly regulated sectors such as finance, healthcare, and public services.
The Learning
Cloud compliance isn’t an end-state; it’s a dynamic obligation shaped by legal, geographical, and operational factors. Data stored outside approved jurisdictions can trigger fines or operational restrictions.
The Fix
- Choose providers with region-specific data storage and clearly defined residency policies.
- Encrypt data at rest and in transit using customer-managed keys.
- Use compliance monitoring tools that continuously evaluate controls against standards like GDPR, HIPAA, and SOC 2.
- For global operations, include a data localization strategy in your provider evaluation checklist.
5. Insecure APIs and Integration Points
The Problem
APIs are the connective tissue of the modern cloud, but they’re also one of its weakest links. Poorly governed or undocumented APIs can expose sensitive workloads to unauthorized access or injection attacks.
A 2024 Salt Security report found a 94% increase in API attacks year-over-year, underscoring how integration complexity multiplies exposure.
The Learning
Every new API is a new entry point. Security must evolve from static firewall rules to dynamic identity and trust models.
Even internal APIs deserve the same scrutiny as external ones.
The Fix
- Adopt a Zero Trust security model that authenticates and validates every request.
- Enforce least privilege access for all API consumers.
- Continuously monitor API activity using behavior analytics to detect anomalies.
- Regularly review and deprecate unused or legacy endpoints.
When security becomes intrinsic to integration, not a layer on top, breaches become much harder to execute.
6. Overdependence on Native Security Tools
The Problem
Cloud providers offer strong native security suites, AWS GuardDuty, Azure Defender, and Google Security Command Center, but relying solely on them creates a false sense of safety.
These tools provide visibility within their ecosystem but rarely correlate events across multiple clouds or hybrid architectures.
The Learning
Cloud-native tools are valuable for baseline monitoring, but they don’t replace independent analytics or cross-provider correlation. The security posture must be seen holistically, not per vendor.
The Fix
Integrate third-party security intelligence and SIEM solutions that aggregate logs across providers.
This multi-layered approach enables deeper anomaly detection and incident response.
Additionally, use cloud-agnostic frameworks like the MITRE ATT&CK Cloud Matrix to analyze attack patterns beyond vendor boundaries.
7. Absence of Continuous Risk and Cost Governance
The Problem
Enterprises often treat security and cost optimization as unrelated goals — but in the cloud, they are deeply intertwined.
Over-provisioned resources, redundant storage, and orphaned credentials don’t just waste money; they create exploitable vulnerabilities.
The Cloud Zero Report (2024) found that enterprises waste an average of $18 million annually due to unmonitored cloud operations and misaligned governance.
The Learning
A sustainable cloud strategy aligns FinOps (financial operations) and SecOps (security operations).
Security maturity is not just about patching — it’s about visibility into how every dollar and every instance contributes to compliance and resilience.
The Fix
- Combine cost and risk dashboards to track both performance and exposure.
- Automated unused resource detection and access review.
- Treat sustainability as a metric, the fewer redundant workloads, the lower your attack surface and carbon footprint.
- Conduct quarterly “security cost audits” to measure the ROI of governance improvements.
Conclusion: Cloud Security as an Ongoing Partnership
Choosing a cloud provider isn’t a procurement decision; it’s an ongoing partnership built on trust, accountability, and continuous improvement.
Security in the cloud doesn’t end with migration; it evolves with every new integration, API, and compliance update.
The organizations that thrive in this landscape are not the fastest adopters or the biggest spenders; they are the most disciplined observers. They question every assumption, audit every configuration, and treat cloud security challenges as opportunities for refinement, not as one-time threats.
Security maturity improves when enterprises pair strong internal governance with the right technical guidance. Kansoft assists teams in refining cloud architectures, automating controls, and strengthening AWS cloud migration frameworks. The objective is not complexity, it’s stability. We help reduce noise, prioritise what matters, and ensure cloud environments are resilient from day one.
A secure cloud ecosystem is one where visibility is continuous, compliance is integrated, and accountability is shared.
When enterprises adopt this mindset, cloud migrations become more than modernization’s milestones; they become long-term investments in digital trust, operational sustainability, and future readiness.